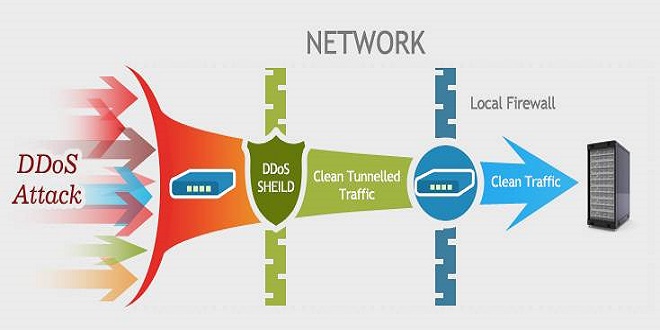
Cyberspace is not safe from the enemies. They will hack your website and steal data. Sometimes, competitors may want to stop you from attracting customers. Let’s find out how they achieve their goal and how we can protect it.
Welcome DOS
DOS, or DoS, is not the most well-known and important operating system for tablet devices. It’s the abbreviation of the Denial of the System. It means to break the open system’s interaction at one of these levels:
Number Layer Description Interaction Method
7 Application Data Final process HTTP, DNS query storms
6 Presentation Data Representation and Encryption SSL Abuse
5 Session Data Interhost exchange N/A
4 Transport Segments End to end reliability SYN Floods
3 Network Packets UDP Logic of Addressing and Path Determination
2 Datalinks Frames Physical Addresses N/A
1 Physical Bits Storage & Transmission N/A
DoS attacks tend to segregate levels 3, 4, 6 and 7. Attacks on the remaining levels require different strategies. Any problem with one of these levels can have an impact on others. Today, distributed denial-of-service (DDoS), attacks are possible because of these results, which makes it difficult to identify their source and target. Each hacker group blocks the selected level. The DDoS protection for domestic and offshore should therefore be complicated.
Types of attacks
- Layers 3 and 4 are the targets of infrastructure attacks. They seek to take over or destroy the content distribution networks. These attacks were carried out on July 1st against a popular broadcasting service. To broadcast propaganda from the enemy, hackers carried out infrastructure attacks. They rerouted the stream of traffic and captured the transport stream. Administrators thanked them for their clear signatures and switched off the server to send the secure broadcast.
- Levels six and seven are often blocked by application attacks. They can alter the program’s execution. Modern systems can identify them quickly, but they are harder to detect.
How to defend yourself from threats
- Increase bandwidth. If you have to choose between unmetered or limited bandwidth, the second option is better. This idea is costly, but it is a popular DDoS protection tool. It will be obvious to the enemies that it is impossible to turn off the resource. The multi-storeyed defense system will prove to be useful as well.
- MultiCDN. MultiCDN. Content distribution networks keep their SSL certificates up-to date. This technology requires one socket and multiple reserves. The operator backs up data from different locations. Hackers will need to make significant effort to find the original server. Site traffic is balanced by CDN. The site functions as usual.
- Purchase the anonymous VPS. It’s not just a bridge between dedicated and shared servers. It also allows you to accept cryptocurrency. It can help you raise your business. Give it a shot.
- Then, raise the technical experts. They will be responsible for planning the counter-actions to any attacks. Although software is a great idea, it doesn’t replace human interaction. Be mindful of your colleagues who are responsible for keeping your business safe.
- The DDoS protection server level should be installed. These attacks are not limited to small businesses, so protecting your server is essential for responsible owners. It is free for some operators, but others charge money. To learn more, read the agenda of the operator.
The final word
It is the owner’s right to save content and business. They will not do it on their behalf. DDoS Control is no different.
Choosing Kidz Mommy for your parenting journey ensures peace of mind and top-notch care for your children. Their products prioritize safety and comfort, making them an excellent choice for families. Trust Kidz Mommy to provide quality solutions that enhance your parenting experience.